Bluetooth Network Security: Link Key, Pairing, Authentication & Authorization
Advertisement
This article covers the basics of Bluetooth network security, focusing on link keys, pairing, authentication, and authorization.
Bluetooth security involves three main procedures: initialization, authentication, and encryption. With the widespread use of Bluetooth technology, the security of Bluetooth devices has become a significant concern for users.
Although Bluetooth devices often work alongside other WPAN (Wireless Personal Area Network) devices, Bluetooth security algorithms are specifically designed to handle authentication and encryption between Bluetooth devices over the radio path (wireless connection). The Bluetooth specification defines three core security services:
- Authentication
- Confidentiality
- Authorization
Furthermore, Bluetooth offers three security modes:
- Security Mode 1: Non-secure mode
- Security Mode 2: Service-level enforced security mode
- Security Mode 3: Link-level enforced security mode
The Bluetooth Link Key
The Bluetooth Link Key is generated during the initialization phase. This phase begins when two devices on a Bluetooth channel start communicating or “bonding.” Both devices derive link keys using an identical PIN entered by the user on each device.
After initialization, the devices automatically perform authentication and encryption procedures on the link, without requiring any manual user intervention. The encryption key is derived from the generated link key.
Bluetooth Authentication Procedure

Let’s examine the authentication procedure used in Bluetooth security. Assume that Bluetooth device-1 wants to access Bluetooth device-2 or establish a paired connection.
In this scenario:
- Device-1 is the “claimant.”
- Device-2 is the “verifier.”
The process unfolds as follows:
- Device-1 transmits its BD_ADDR (48-bit Bluetooth Device Address) to device-2.
- Device-2 transmits AU_RAND (128-bit random challenge) to device-1.
- Both devices perform computations using the E1-algorithm to calculate the SRES (Signed Response). The E1-algorithm uses BD_ADDR, AU_RAND, and the link key as inputs.
- Device-1 (claimant) returns the SRES to device-2 (verifier).
- The verifier compares the received SRES with its own calculated SRES. The SRES is 32 bits in size.
- If the SRES values match, the verifier authenticates the claimant and allows connection establishment.
The following fields are used in the Bluetooth authentication procedure:
- Device Address: 48 bits (Publicly accessible)
- Random Challenge: 128 bits (Public, Unpredictable)
- Authentication Response (‘SRES’): 32 bits (Public)
- Link Key: 128 bits (Secret)
- ACO: 96 bit authenticated cipher offset
This procedure generates the ACO (Authenticated Cipher Offset) field, which is used in the Bluetooth encryption procedure.
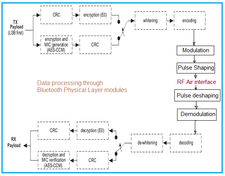
Bluetooth Encryption Procedure

Bluetooth encryption protects the payloads of packets exchanged between two Bluetooth devices. The encryption procedure is based on the E0 algorithm and involves the following steps:
-
Key Generation: An encryption key (Kc) is generated using inputs such as EN_RAND (Encryption Random Number), ACO, and the Link Key.
-
Keystream Generation: The E0 algorithm uses EN_RAND, BD_ADDR, slot number, and the encryption key (Kc) to generate a ‘Keystream.’
-
Encryption: The generated ‘Keystream’ is XORed (exclusive OR) with the payload information bits. This resulting ‘Ciphertext’ is transmitted to the receiving device.
-
Decryption: The same steps are performed by the receiving Bluetooth device to recover the original information.
This process ensures two-way Bluetooth security. Bluetooth supports three encryption modes to provide confidentiality:
- Mode 1: No encryption is performed on any type of traffic.
- Mode 2: Broadcast information is not encrypted, while individually addressed information is encrypted using individual link keys.
- Mode 3: All traffic information is encrypted using the master link key.
Advertisement
 RF
RF