AES: Advantages and Disadvantages of Advanced Encryption Standard
Advertisement
This page covers the advantages and disadvantages of AES (Advanced Encryption Standard). It outlines the benefits and drawbacks, while also providing an introduction to AES basics.
What is AES? (Introduction)
- AES stands for Advanced Encryption Standard.
- It’s a FIPS (Federal Information Processing Standards) approved cryptographic algorithm used to protect electronic data.
- AES is a symmetric block cipher, meaning the same key is used for both encryption and decryption.
- The encryption process transforms data into ciphertext, while decryption converts ciphertext back into its original form.
- The AES algorithm uses different key lengths (128, 192, or 256 bits) to encrypt and decrypt data in blocks of 128 bits.
- AES is implemented in both hardware and software to protect digital information (data, voice, video, etc.) from attacks and eavesdropping.
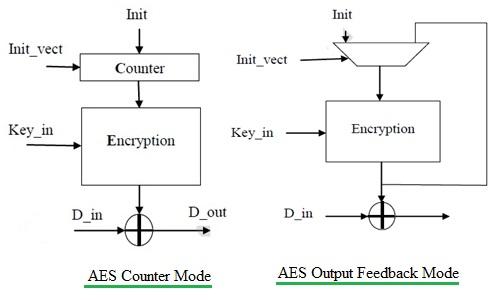
Figure 1 depicts two modes of AES algorithm viz. CTR (counter) mode and OFB (Output Feed Back) mode.
In CTR (Counter) mode, the output of the Counter is the input for the Encryption core and an initialization vector is used to initialize the counter. Input data is encrypted by XOR’ing it with the output of the Encryption module. The data coming out after this operation is called cyphertext. Decryption reverses the encryption operation.
In OFB mode, the output of the Encryption operation is fed back to the input of the Encryption Core. An initialization vector is used for the first iteration. Input data is Encrypted by XOR’ing it with the output of the Encryption module.
| AES type | Key Length (Nk words) | Block Size (Nb words) | Number of rounds (Nr) |
|---|---|---|---|
| AES-128 | 4 | 4 | 10 |
| AES-192 | 6 | 4 | 12 |
| AES-256 | 8 | 4 | 14 |
The table above mentions three types of AES based on key lengths used in the algorithm.
Benefits or Advantages of AES
Here are some of the advantages of using AES:
- Robust Security Protocol: AES is implemented in both hardware and software, making it a highly robust security protocol.
- Strong Encryption: It uses larger key sizes (128, 192, and 256 bits) for encryption, making the AES algorithm more resistant to hacking attempts.
- Wide Application: AES is a common security protocol used in various applications, including wireless communication, financial transactions, e-business, and encrypted data storage.
- Widely Used: It’s one of the most widely used commercial and open-source solutions globally.
- Personal Information Security: AES makes it difficult to hack personal information.
- Difficult to Hack: Breaking a 128-bit AES encryption would require approximately 2128 attempts, making it a very safe protocol.
Drawbacks or Disadvantages of AES
Here are some of the disadvantages of using AES:
- Simple Algebraic Structure: Its algebraic structure is considered too simple.
- Consistent Encryption: Every block is always encrypted in the same way, potentially making it vulnerable to certain attacks if not implemented carefully.
- Software Implementation Challenges: It can be difficult to implement efficiently in software.
- Counter Mode Complexity: Implementing AES in counter mode can be complex in software, requiring careful consideration of both performance and security.
Advertisement
 RF
RF



